A lot of people use Bitlocker for full-disk encryption of their hard drives. For extra security you might want to be prompted for a PIN when you unlock your hard drive, because allowing attackers to boot your system without authentication might open up extra attack vectors. Setting a PIN can be easily accomplised if you know how… 🙂
The below instructions are exact for Windows 10, but they are very similar in Windows 7, too.
Launch the Local Group Policy Editor by typing gpedit.msc into your Windows search, then when it has been found right-click on it and select Run as administrator from the pop-up menu. Then maneuver to the following path in the left “folder” pane:
Local Computer Policy > Computer Configuration > Administrative Templates > Windows Components > Bitlocker Drive Encryption > Operating System Drives.
This is what it looks like if you did it correctly:
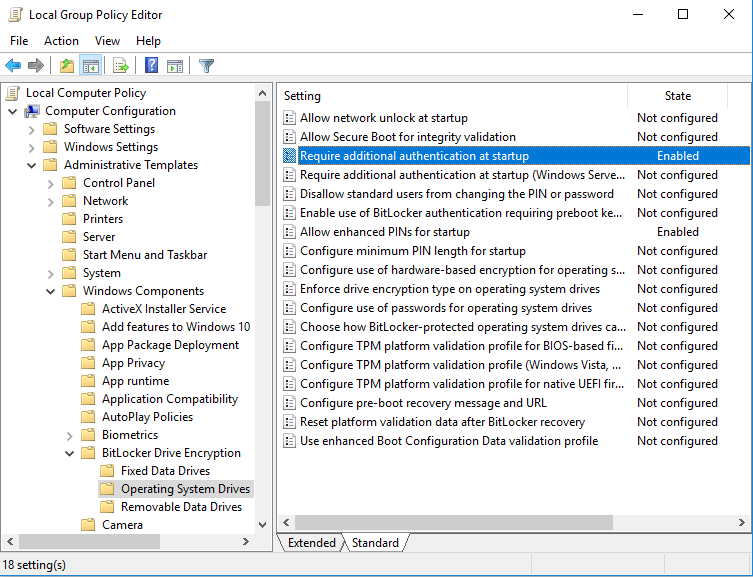 Then double-click on the setting
Then double-click on the setting Require additional authentication at startup, and you see the following dialog:
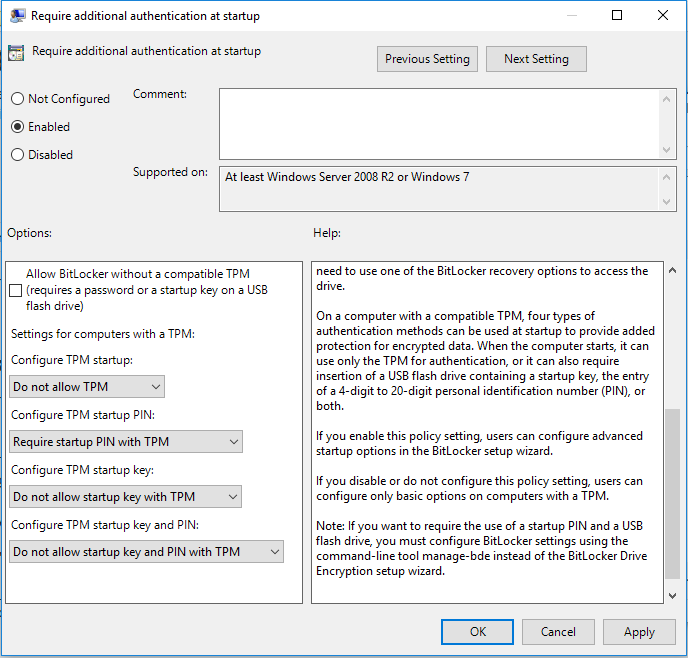 Now change option
Now change option Configure TPM startup PIN to read:
Require startup PIN with TPM
Then reboot. Now you can right-click on your system drive and select Set Bitlocker PIN or Change Bitlocker PIN (I forgot to take a screenshot of this last step, so I’m not 100% how exactly this looked like, but it should be obvious) from the pop-up menu.
You’re done. Wasn’t that easy?
Please leave a message if this was helpful.